Establishing Client <-> Server Communication:
The WSUS provides various options to manage client <-> server communication. One of the feature is to classify the clients into groups and let them receive custom set of updates. For this one need to
- create a Computers Group in WSUS console and
- configure client side targeting on computers to auto join the selected group
- Creating Computer group in WSUS console:
Classifying/Grouping client computers: This is required if you want to deploy a different set of updates to these selected group of computers. A classical example would be that you would like to run the newly released updates just on a selected group of computers called “QA Workstations”. To create a new computer group,
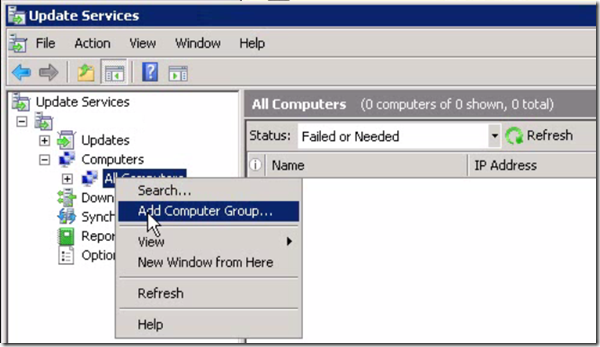
- Launch Update Services console
- Goto Computers
- Right click on “All Computers”
- Click “Add Computer Group…”
Configuring Client Side Targeting on client computers
By default all client computers communicating to WSUS server will get assigned into “Unassigned Computers” group. And one needs to manually move them around to intended groups manually and keeping these updated going forward would time consuming. To avoid this, you can configure the client computers to automatically go and join to a group to which they are configured. This is called Client Side Targeting. To configure Client Side Targeting, have it enabled on the server and then deploy config settings to the clients
Enable Client Side Targeting:
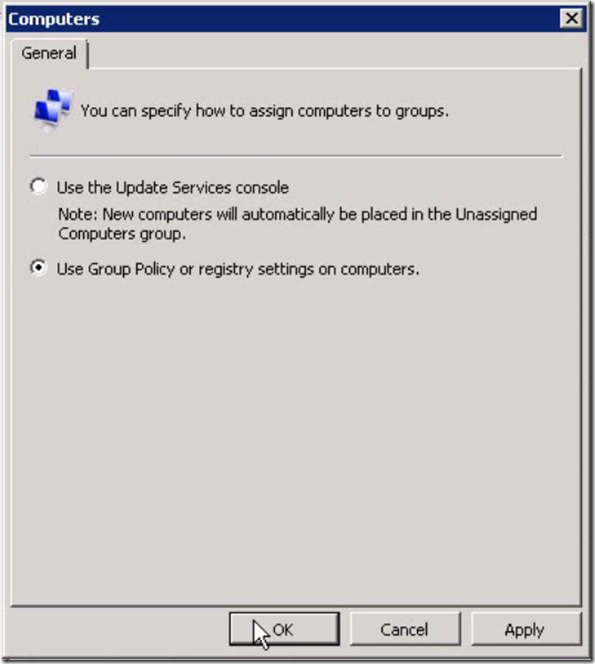
- Launch Update Services console
- Goto Options
- Click Computers

- Select “Use Group Policy or registry settings on computers.”
- d
Deploying WSUS client side targeting settings to client computers:
Create new GPO or choose any of the existing one as per your requirement:
- In GPO Editor navigate to “Computer ConfigurationAdministrative TemplatesWindows ComponentsWindows update”
- open “Enable client-side targeting” setting and specify the group name that you just created.
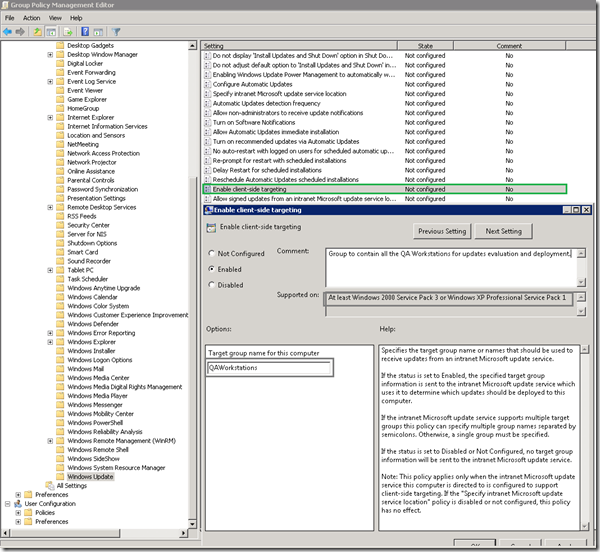
- As mentioned above by policy setting description, you need to configure “Specify intranet Microsoft Update service location”

Specifies the target group name or names that should be used to receive updates from an intranet Microsoft update service.
If the status is set to Enabled, the specified target group information is sent to the intranet Microsoft update service which uses it to determine which updates should be deployed to this computer.
If the intranet Microsoft update service supports multiple target groups this policy can specify multiple group names separated by semicolons. Otherwise, a single group must be specified.
If the status is set to Disabled or Not Configured, no target group information will be sent to the intranet Microsoft update service.
Note: This policy applies only when the intranet Microsoft update service this computer is directed to is configured to support client-side targeting. If the "Specify intranet Microsoft update service location" policy is disabled or not configured, this policy has no effect.
- you need to specify WSUS server that you want these group of computers to communicate with
Specifies an intranet server to host updates from Microsoft Update. You can then use this update service to automatically update computers on your network.
This setting lets you specify a server on your network to function as an internal update service. The Automatic Updates client will search this service for updates that apply to the computers on your network.
To use this setting, you must set two servername values: the server from which the Automatic Updates client detects and downloads updates, and the server to which updated workstations upload statistics. You can set both values to be the same server.
If the status is set to Enabled, the Automatic Updates client connects to the specified intranet Microsoft update service, instead of Windows Update, to search for and download updates. Enabling this setting means that end users in your organization don’t have to go through a firewall to get updates, and it gives you the opportunity to test updates before deploying them.
If the status is set to Disabled or Not Configured, and if Automatic Updates is not disabled by policy or user preference, the Automatic Updates client connects directly to the Windows Update site on the Internet.
Note: If the "Configure Automatic Updates" policy is disabled, then this policy has no effect.
<li></li> <li>Assign the GPO policy to the required OUs/groups</li> <li></li> <p> </p> <p><strong><u>Approving Updates Manually/Automatically:</u></strong></p> <p>Updates will be pushed/deployed to clients by the WSUS server only upon its approval. </p> <p>For automatic approvals, go to WSUS console > Options > Automatic Approvals</p> <p><a href="http://gunnalag.files.wordpress.com/2012/04/image65.png"><img style="background-image:none;border-bottom:0;border-left:0;padding-left:0;padding-right:0;display:inline;border-top:0;border-right:0;padding-top:0;" title="image" border="0" alt="image" src="http://gunnalag.files.wordpress.com/2012/04/image_thumb65.png" width="600" height="376" /></a></p> <p>You’ll be presented with the list of Automatic Approvals Rules along with the default rule</p> <p><a href="http://gunnalag.files.wordpress.com/2012/04/image66.png"><img style="background-image:none;border-bottom:0;border-left:0;padding-left:0;padding-right:0;display:inline;border-top:0;border-right:0;padding-top:0;" title="image" border="0" alt="image" src="http://gunnalag.files.wordpress.com/2012/04/image_thumb66.png" width="555" height="619" /></a></p> <p>Click Edit rule to choose/modify the predefined set of pr
oducts and classifications for approvals
You can also set to which group does this Automatic Approval of selected products update to be deployed. The default is set to “All Computers”
Manual approvals of updates:
Goto WSUS console > Updates > All Updates or select other appropriate categories
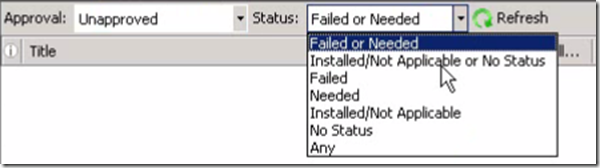
You can filter the results based on various status as shown below
Double click on any of the update(s). You’ll see “Approve Updates” wizard as shown below.
Select the group to which you’d like to have this update approved and then click on “Approve for install”
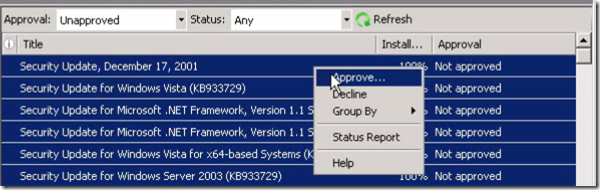
You can also approve updates, by right click> “Approve…”
WSUS Group Policy Settings:
|
Sl.No |
Setting |
|
1 |
Do not display ‘Install Updates and Shut Down’ option in Shut Down Windows dialog box |
|
2 |
Do not adjust default option to ‘Install Updates and Shut Down’ in Shut Down Windows dialog box |
|
3 |
Enabling Windows Update Power Management to automatically wake up the system to install scheduled updates |
|
4 |
Configure Automatic Updates |
|
5 |
Specify intranet Microsoft update service location |
|
6 |
Automatic Updates detection frequency |
|
7 |
Allow non-administrators to receive update notifications |
|
8 |
Turn on Software Notifications |
|
9 |
Allow Automatic Updates immediate installation |
|
10 |
Turn on recommended updates via Automatic Updates |
|
11 |
No auto-restart with logged on users for scheduled automatic updates installations |
|
12 |
Re-prompt for restart with scheduled installations |
|
13 |
Delay Restart for scheduled installations |
|
14 |
Reschedule Automatic Updates scheduled installations |
|
15 |
Enable client-side targeting |
|
16 |
Allow signed updates from an intranet Microsoft update service location |